Standard Access Lists
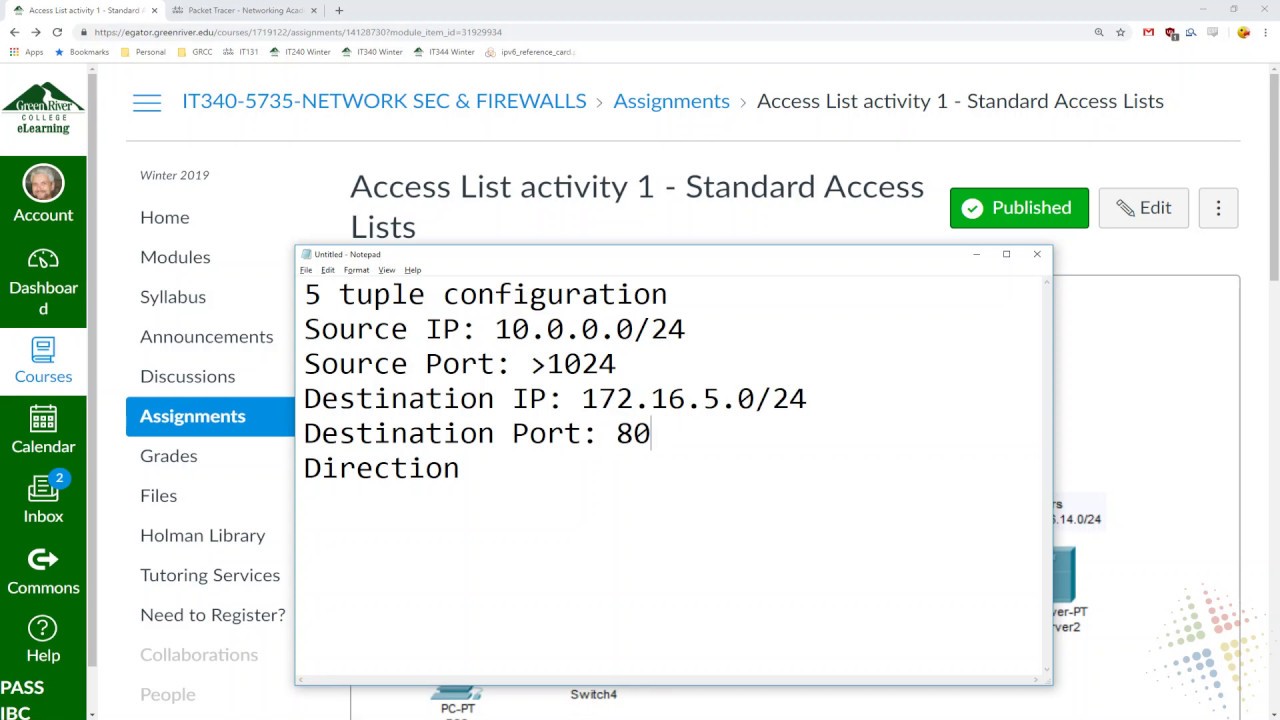
In these standard access list activities we walk through how firewalls evaluate traffic and the 5 tuples used to permit or deny traffic. We then walk through an example activity using packet tracer.
Second activity using Standard Access Lists. This walks through evaluating our firewall requirements, viewing the flow of data, and identifying the rules needed. We then create access lists in Packet Tracer and validate the functionality.