Palo Alto Zones, Interfaces, and Routers – Overview
Palo Alto firewalls can be very simple to use and implement, or they can be very difficult. Because there are so many possible components and areas of configuration in these firewalls, understanding the basic features can be helpful.
Management vs Data Plane
Most network equipment is split into 2 (or more) basic components: a management plane and a data plane. The data plane is used by end users. This is where end users connect desktops, laptops, mobile devices, or servers. The firewall is configured to monitor and manage traffic on the data plane.
The management plane is primarily responsible for managing the device. This means that when an administrator wants to change something, such as an IP address or firewall rule, they connect to the management plane. All management related activities: configurations, authentication, updates, and so on, are performed through the management plane. Normal users are almost always excluded from accessing the management plane as a basic security concept.

In the image above, the network ports on the top half of the Palo Alto are designated for the Data Plan. The ports on the bottom half of the device are designated for the management plane. NOTE: These ports can be configured differently, but this is the general configuration
Interfaces
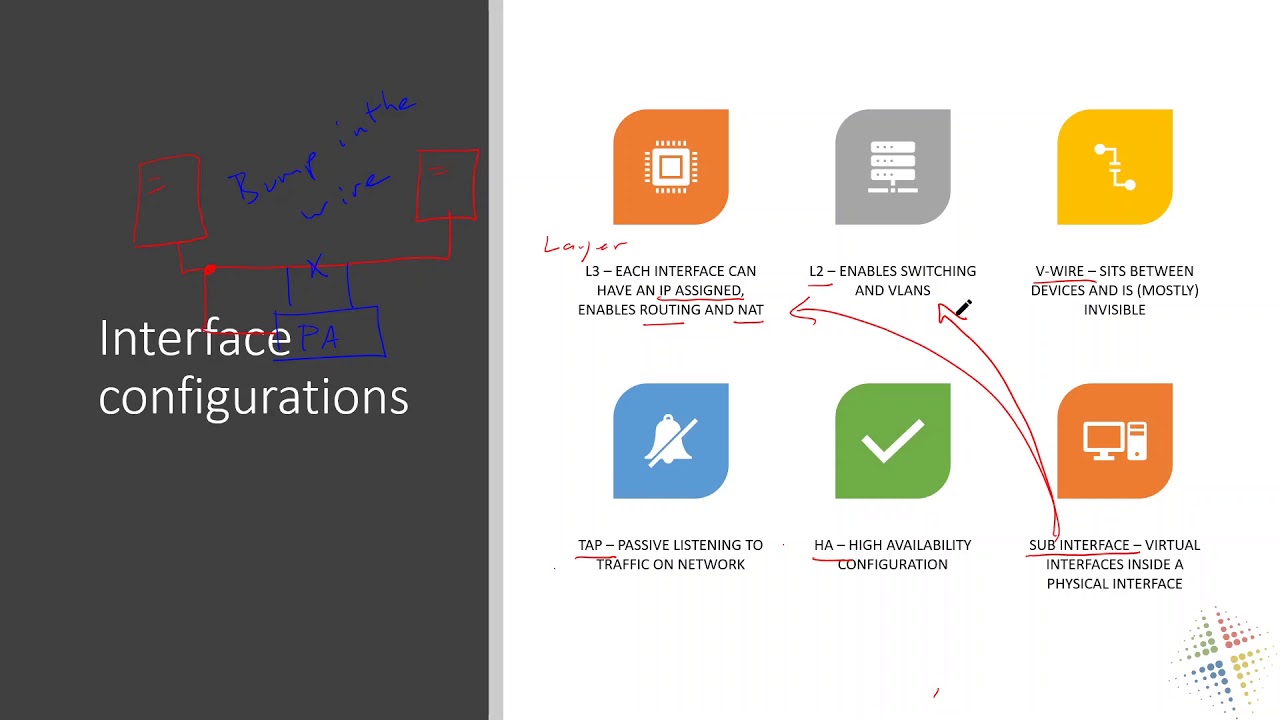
The data plane interfaces can be configured in a variety of ways depending on your needs:
Layer 3 – A layer 3 interface allows the port on the firewall to have an IP address assigned to it. Once an address is assigned, all IP related functions, such as routing and NAT, can be performed by that interface.
Layer 2 – A layer 2 interface allows the port to act similar to a network switch. This can then switch traffic to different ports or VLANs as needed.
V-Wire – A v-wire, or “virtual wire”, interface sits between devices and is mostly invisible to the devices and traffic. Sometimes referred to as a “bump in the wire”.
TAP – A TAP interface is designed to passively monitor traffic and report. This is often used to inspect existing equipment and interfaces without changing the infrastructure.
HA – a HA, or “High Availability” interface is used to make the Palo Alto device redundant. The HA interface is used to copy configuration changes to the backup device, and act as a “heartbeat” to confirm availability.
Sub Interface – A sub interface is a virtual interface, often times tied to a physical interface. One of the most common uses of a sub interface would be for VLANs on a trunk connection
Routing
Palo Alto devices can enable routing between Layer 3 interfaces by use of a “Virtual Router”. The virtual router is attached to interfaces and learn routes through various methods. Because this is a firewall and not a router, the default configuration is to deny routing traffic unless explicitly permitted.
By using virtual routers, the Palo Alto can act as multiple routers at the same time. This is useful to isolate various departments, labs, or customers from each other. Additionally, the use of virtual routers allow the duplication of IP networks on different routers.
Zones
Zones are used to help abstract physical interfaces to friendly names such as Desktops, Servers, DMZ, and so on. Rules and policies are applied to zones, making the configuration easier to create and modify since we can use friendly names.
A single zone can contain 1 or more interface, allowing configurations to be applied consistently.