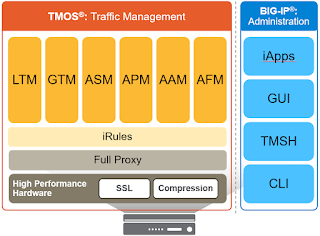
F5-CA – Application Delivery Fundamentals – F5 Solutions and Technology
Objective 2.01: Articulate the role of F5 products
Explain the purpose, use, and benefits of APM, LTM, ASM, GTM
Access Policy Manager
APM provides valuable insight and policy-based control over who is on the network and what applications they are using.
Local Traffic Manager
LTM provides intelligent traffic management, ensuring peak application performance and increasing operational efficiency.
Application Security Manager
ASM offers an agile, certified web application firewall to protect and optimize all of your applications with advanced application and location visibility and protection.
Global Traffic Manager – BIG-IP DNS
BIG-IP DNS directs users to the nearest data center that will provide the best application experience. Using high-performance DNS services, BIG-IP DNS secures your DNS infrastructure from attacks.
Advanced Firewall Manager
AFM inspects traffic that is both entering and leaving your datacenter, ensuring protection of sensitive data such as social security numbers and credit card information.
Application Acceleration Manager
AAM speeds up application delivery, controls the growth of bandwidth needs, particularly for video, and off loads additional processor-intensive tasks from the server.
More information:
Access Policy Manager (APM)
Application Security Manager (ASM)
Local Traffic Manager (LTM)
Global Traffic Manager (GTM)
Enterprise Manager (EM)
F5 White Papers
F5 Datasheets
Objective 2.02: Explain the purpose, use, and advantages of iRules
Explain the purpose of iRules
An iRule is a powerful and flexible feature of BIG-IP devices based on F5’s exclusive TMOS architecture. iRules provide you with unprecedented control to directly manipulate and manage any IP application traffic. iRules utilizes an easy to learn scripting syntax and enables you to customize how you intercept, inspect, transform, and direct inbound or outbound application traffic.
Explain the advantages of iRules
iRules is a highly customized, Tcl-based scripting language that allows you complete programmatic access to the traffic on the wire. If you’re looking to inspect, analyze, modify, route, re-direct, discard, manipulate, re-play, mirror or…just about anything else you can think of, chances are you can do it with an iRule. It offers incredible flexibility and control that makes it possible to do unbelievably cool stuff with your F5 gear. iRules gives you the ability to write business logic into your network layer, and that is a powerful and liberating thing.
Given a list of situations, determine which would be appropriate for the use of iRules
More information:
iRules 101
Getting Started with iRules
Objective 2.03: Explain the purpose, use, and advantages of iApps
Explain the purpose of iApps
Local Traffic Manager includes F5 iApps, a powerful set of features that enable you to manage application services rather than individual devices and objects. iApps gives you greater visibility and control over application delivery—and helps you deploy in hours rather than weeks. This application-centric approach aligns the network with your applications and adapts application delivery to business needs.
Explain the advantages of iApps
iApps, similar to wizards, guide the administrator through setting up of common configurations. However, unlike a wizard, iApps can be re-run multiple times to adjust or update the configurations.
Given a list of situations, determine which would be appropriate for the use of iApps
If there is an iApp appropriate for your environment, use it. The only exception might be when you wish to customize the configuration after the fact, and dont wish to lose that customization when making updates in the future.
More information:
Objective 2.04: Explain the purpose of and use cases for full proxy and packet forwarding/packet based architectures
Describe a full proxy architecture
The reason there is a distinction made between “proxy” and “full-proxy” stems from the handling of connections as they flow through the device. All proxies sit between two entities – in the Internet age almost always “client” and “server” – and mediate connections.
A full-proxy maintains two separate session tables – one on the client-side, one on the server-side. There is effectively an “air gap” isolation layer between the two internal to the proxy, one that enables focused profiles to be applied specifically to address issues peculiar to each “side” of the proxy.
Describe a packet forwarding/packet based architecture
A network device with a packet-based (or packet-by-packet) design is located in the middle of a stream of communications, but is not an endpoint for those communications; it just passes the packets through. Often a device that operates on a packet-by-packet basis does have some knowledge of the protocols flowing through it, but is far from being a real protocol endpoint. The speed of these devices is primarily based on not having to understand the entire protocol stack, short-cutting the amount of work needed to handle traffic. For example, with TCP/IP, this type of device might only understand the protocols well enough to rewrite the IP addresses and TCP ports; only about half of the entire stack.
Given a list of situations, determine which is appropriate for a full proxy / packet based architecture
More information:
Full Proxy Architecture
Packet-Based vs Full Proxy
SNAT
Auto Last Hop
Virtual Server Types
Objective 2.05: Explain the advantages and configurations of high availability (HA)
Explain active/active
For certain network environments, you might want to configure an active-active configuration. The basic configuration procedure is similar to the configuration procedure for an active-standby configuration, except that you must set the redundancy mode on both units to Active.
Unlike an active/standby configuration, which is designed strictly to ensure no interruption of service in the event that a BIG-IP system becomes unavailable, an active-active configuration has an additional benefit. An active-active configuration allows the two units to simultaneously manage traffic, thereby improving overall performance.
A common active-active configuration is one in which each unit processes connections for different virtual servers. For example, you can configure unit 1 to process traffic for virtual servers A and B, and configure unit 2 to process traffic for virtual servers C and D. If unit 1 becomes unavailable, unit 2 begins processing traffic for all four virtual servers.
Explain active/standby
When a redundant system is in active/standby mode, one unit is active, that is, accepting and processing connections on behalf of the redundant system, while the other unit is idle (that is, in a standby state).
When failover occurs, the standby unit becomes active, and it normally stays active until failover occurs again, or until you force it into a standby state. Forcing the unit into a standby state automatically causes the other system to become active again, if possible.
For example, you can configure unit 1 to process traffic for virtual servers A and B. The standby unit monitors the active unit, and if communications fail, the standby unit initiates a failover and becomes the active unit. The newly-active unit then begins processing traffic for both virtual servers.
Explain the benefits of deploying BIG-IP devices in a redundant configuration
A redundant system is a type of BIG-IP® system configuration that allows traffic processing to continue in the event that a BIG-IP system becomes unavailable. A BIG-IP redundant system consists of two identically-configured BIG-IP units. When an event occurs that prevents one of the BIG-IP units from processing network traffic, the peer unit in the redundant system immediately begins processing that traffic, and users experience no interruption in service.